BSides London 2013 Challenge 5
Another BSides London 2013 challenge! I didn't enter as I had already managed to get my hands on a ticket at the time this one was released. I did, with the help of some colleagues, complete the challenge to fill some spare time I had at the weekend.
There was no back story associated with this challenge. You were simply provided with a PDF document, and told to follow the clues until you came across a secret code, a subject line and an email address to which these could be sent.
I should also add that although this post shows the most direct route to the final answer, we did find ourselves following a few red herrings and banging our heads against a few proverbial brick walls.
Stage 1: The text of the PDF document give clues as to how to complete this stage. Within the seemingly random text is this string:
There is also this string within the body of the text:





Stage 9: KPNG.png appeared to be a standard image file, but by tweaking the contrast, inverting the colours and changing the background colour to black the following could be seen:

There was no back story associated with this challenge. You were simply provided with a PDF document, and told to follow the clues until you came across a secret code, a subject line and an email address to which these could be sent.
I should also add that although this post shows the most direct route to the final answer, we did find ourselves following a few red herrings and banging our heads against a few proverbial brick walls.
Stage 1: The text of the PDF document give clues as to how to complete this stage. Within the seemingly random text is this string:
- guvfgrkgvfwhfgnqvfgenpgvbasebzgurernypunyyratr
When decoded using ROT13 this becomes:
- thistextisjustadistractionfromtherealchallenge
- checkth3m3taD4ta
OK - let's take a look at the metadata. Running strings -n 10 KPMGSidesLondon2013CTF.pdf found the following in the document's metadata:
- <xmpMM:DocumentID>40be4e59b9a2a2b5dffb918c0e86b3d701b6e20344b68835c5ed1ddedf20d5318fc42c6ddf9966db3b09e84365034357b04ec0ade3d49b4a079f0e207d5e2821639bae9ac6b3e1a84cebb7b403297b7955f195813a158d82e2934cfac569575d8c4291f6956da81515a5c0caec2976d07d0db380a5b95a8ba1da0bca241abda1f2bab06044281a8c660c441ff4dc795201b6e20344b68835c5ed1ddedf20d5310cc175b9c0f1b6a831c399e26977266198defd6ee70dfb1dea416cecdf391f58be1ab1632e4285edc3733b142935c60b92eb5ffee6ae2fec3ad71c777531578f865c0c0b4ab0e063e5caa3387c1a8741e358efa489f58062f10dd7316b65649e69eb76c88557a8211cbfc9beda5fc0622db95e8e1a9267b7a1188556b2013b33415290769594460e2e485922904f345d9fbbaa4cc515bc46e0c12e82a31df736c4ca4238a0b923820dcc509a6f75849bc81e728d9d4c2f636f067f89cc14862ce358efa489f58062f10dd7316b65649e7b8b965ad4bca0e41ab51de7b31363a1865c0c0b4ab0e063e5caa3387c1a8741a87ff679a2f3e71d9181a67b7542122cc4ca4238a0b923820dcc509a6f75849b</xmpMM:DocumentID>
- welcome to the challenge you should look at going to a site like bit.ly/12tni41
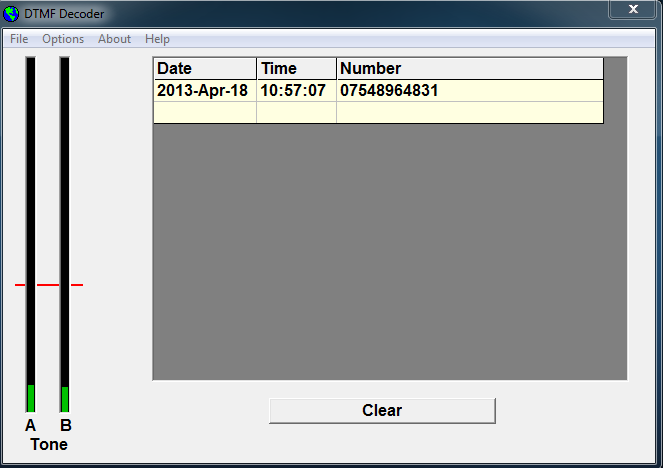
Stage 3: Calling 07548964831 went straight to voicemail. The voicemail message contained a backmasked audio sample. The message was recorded and reversed using Audacity. The reversed audio contained a link to a Twitter profile.
Stage 4: King Capture's Twitter account contained one tweet.
The text in the King Capture’s only tweet was decoded as ASCII hexadecimal:
- 64:48:4a:35:49:48:42:68:63:33:52:6c:59:6d:6c:75:4c:6d:4e:76:62:51:3d:3d
- dHJ5IHBhc3RlYmluLmNvbQ==
- try pastebin.com
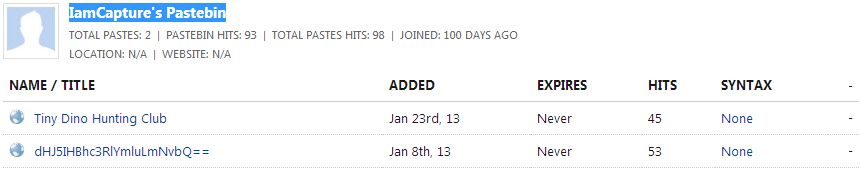
Stage 5: IamCapture's Pastebin contained two entries:
The entry titled dHJ5IHBhc3RlYmluLmNvbQ== contains a ROT13 encoded string:
- GEL CBFGVAT UVFGBEL.
- TRY POSTING HISTORY.
The entry titled Tiny Dino Hunting Club contains a short paragraph:
- Tiny Dino Hunting Club has been blogging some cool things.
Stage 6: King Capture’s blog and contains one entry titled “Awesome reverse image”:
Using Google Image Reverse Search found that the image was also hosted on the Giant Dino Hunting Blog, and this blog contained one other entry that contained a link to a file called capture.pcap.
Stage 7: capture.pcap was a packet capture file containing a HTTP session between 192.168.0.150 and 192.168.0.104. Four GET requests were made by 192.168.0.150 to 192.168.0.104:
- GET / HTTP/1.1
- GET /favicon.ico HTTP/1.1
- GET a.html HTTP/1.1
- GET /favicon.ico HTTP/1.1
- Select one of the packets that form part of the TCP session
- Click File > Export Objects > HTTP
- Select the file of interest (a.html in this case)
- Click Save As, select a path and filename, and click Save
It was possible to reconstruct these to form what looks like a QR code:
It's clear that the image has been warped and attempts to read it using QR scanners failed. Using the Gimp image manipulator, the QR code was unwarped using the IWarp filter. By setting a maximum radius, and a slight clockwise shift, the QR code was unwarped just enough to be legible by a QR reader:
The QR code contained a link to a file on MegaUpload.
Stage 8: The file hosted on MegaUpload was 1050.zip. This file contained a gzip file called 1050.3.gz. 1050.3.gz contained a file called 1050.2.bz2. 1050.2.bz2 contained a file called 1050.1.tar. 1050.1.tarcontained a file called 1049.3.gz. It's a decompression bomb! To avoid wasting time the following script was created to perform the decompression process:
#!/bin/bash
unzip 1050.zip
for i in {1050..0}
do
gunzip --force $i.3.gz && mv $i.3 $i.2.bz2 && bunzip2 $i.2.bz2 && mv $i.2 $i.1.tar && tar xvf $i.1.tar
done
The script reached 1000.2.bz2 when it failed to decompress. Running the Linux file command found that this was because the file was actually a password protected 7z compressed file containing another file called 999.7z. The file was renamed to 1000.7z and the following BASH script run to brute force the password:
#!/bin/bash
while read line; do
7z e -y -p$line zipped.7z
if [ $? == 0 ]; then
echo "$line"
exit
fi
echo "$line"
done < /root/passwords
This found that the password was "password999". It appeared that the password to decompress the 7z compressed file was the "password" concatenated with the name of the file contained within. The following script was created to perform these operations:
for i in {1000..1}
do
7z e -y -ppassword$i $i.7z
done
The script executed until it reached 500.zip when it failed. This file was also password protected. Wrote a similar script to decompress the ZIP files:
for i in {1000..1}
do
unzip -P password$i $i.zip
done
The script executed until it reached 0.zip when it failed. This compressed file contained an image file called KPNG.png. This final compressed file was also password protected. The password was found to be simply "kpng".Stage 9: KPNG.png appeared to be a standard image file, but by tweaking the contrast, inverting the colours and changing the background colour to black the following could be seen:
We made it!
- Email:k.bsides.ctf@gmail.com
- Subject: 4544eb2d4cb5dd50a18a6a396cc2eb5d
- Body: Stage completed - 2fc57d6f63a9ee7e2f21a26fa522e36b
Thanks to KPNG for putting together a great challenge!


Comments
Post a Comment